Note: If you're looking for methods on "how to bypass anti-virus software" - this page isn't for you. This is an analysis about the effects of using the differences in Metasploit framework encoders:
- How do different encoders compare with the detection rate of anti-virus?
- Is there a relationship with increasing the encoded amount of time? Does it get detected less?
- By altering the payload, will this have a affect?
- If a different "template" is used, would it still detected the same amount of times?
- Does encoding make the file detected more than if it wasn't encoded at all?
- Will the payload's operating system matter?
- Which anti-virus product was able to detect the most (and the least) amount?
- Brief
- Method
- Commands
- Results
- Table 1 - Results Summary
- Table 2 - Anti-Virus Results
- Graph 1 - Anti-Virus Performance
- Graph 2 - Detection Rate for "generic/custom-calc.exe"
- Graph 3 - Detection Rate for "OS Bind Shell"
- Graph 4 - Detection Rate for "Windows Meterpreter Bind (1 Iteration)"
- Graph 5 - Detection Rate for "Windows payloads (1 Iteration)"
- Graph 6 - Iterations From 1 to 100
- Graph 7 - Range of Encoders Efficiency
- Graph 8 - Total Detects
- Graph 9 - Total Rate Of Detection
- Summary
- Conclusion
Brief
The Metasploit framework was used to generate a various combination of executable programs which would grant remote access (a 'backdoor') to the machine.
Upon the creation of each file, the output was uploaded to VirusTotal which was scanned using multiple anti-virus products to reveal if any vendor was able to detect the "malicious malware".
Method
As Metasploit customizes the output it creates, various settings were altered slightly each time upon creation, thus making each output unique slightly. In this experiment there were:
- 27x Encoders (Which algorithm to use)
- 5x Iterations (How many times to encode)
- 20x Payloads (What function to execute)
- 5x Templates (Which file to base the output around)
By looping through each of the above, each time modifying it once, the result produced 6750 unique files (note: It's not the 'full' amount as some factors are OS dependant, example; you can't use a windows program for a Linux template).
Each file was then uploaded to VirusTotal, which scans the file using 44 anti-virus products (note: The signatures used on virustotal are more 'sensitive' rather than the ones found publicly. Therefore they have a higher detection rate). VirusTotal services was used to save time as it automates the whole procedure and creates a report rather than manually scanning each file ourselves with every vendor.
VirusTotal has a public API feature, so to take advantage of this, a script (bmmvtu.py), was developed to automate this procedure, allowing for multiple files to scanned without any interaction.
Below is a list of all the variables used:
| Anti-Virus Products | Encoders | Iterations | Payloads | Templates (MD5) |
|---|---|---|---|---|
| AhnLab-V3 | cmd/generic_sh | 1 | generic/custom (Linux & OSX & Windows) | calc.exe (0adf66d67ba98090cd5ce9166a7e323f) |
| AntiVir | cmd/ifs | 5 | linux/x86/meterpreter/bind_tcp-default | cmd.exe (6d778e0f95447e6546553eeea709d03c) |
| Antiy-AVL | cmd/printf_php_mq | 10 | linux/x86/meterpreter/reverse_tcp-default | default - template_x86_windows.exe (99addd5248236a60aeddbc35024cd2ab) |
| Avast | generic/none | 25 | linux/x86/shell/bind_tcp-default | default - template_x86_linux.bin (8892430dd8bdfdc29abdcba9560b4d66) |
| Avast5 | mipsbe/longxor | 100 | linux/x86/shell/reverse_tcp-default | default - template_x86_darwin.bin (3c1738e7a0f1428d0ddb7d4e15cd4f1b) |
| AVG | mipsle/longxor | linux/x86/shell_bind_tcp-default | mspaint.exe (a68da24239c7ba6c424e1aeae7aa3e7a) | |
| BitDefender | php/base64 | linux/x86/shell_reverse_tcp-default | write.exe (bb75ed2cea65d2de97e88fde1b1a0bf8) | |
| ByteHero | ppc/longxor | linux/x86/shell_reverse_tcp2-default | ||
| CAT-QuickHeal | ppc/longxor_tag | osx/x86/shell_bind_tcp-default | ||
| ClamAV | sparc/longxor_tag | osx/x86/shell_reverse_tcp-default | ||
| Commtouch | x64/xor | osx/x86/vforkshell/bind_tcp-default | ||
| Comodo | x86/alpha_mixed | osx/x86/vforkshell/reverse_tcp-default | ||
| DrWeb | x86/alpha_upper | osx/x86/vforkshell_bind_tcp-default | ||
| Emsisoft | x86/avoid_utf8_tolower | osx/x86/vforkshell_reverse_tcp-default | ||
| eSafe | x86/call4_dword_xor | windows/meterpreter/bind_tcp | ||
| eTrust-Vet | x86/context_cpuid | windows/meterpreter/reverse_tcp | ||
| F-Prot | x86/context_stat | windows/shell/bind_tcp | ||
| F-Secure | x86/context_time | windows/shell/reverse_tcp | ||
| Fortinet | x86/countdown | windows/shell_bind_tcp | ||
| GData | x86/fnstenv_mov | windows/shell_reverse_tcp | ||
| Ikarus | x86/jmp_call_additive | |||
| Jiangmin | x86/nonalpha | |||
| K7AntiVirus | x86/nonupper | |||
| Kaspersky | x86/shikata_ga_nai | |||
| McAfee | x86/single_static_bit | |||
| McAfee-GW-Edition | x86/unicode_mixed | |||
| Microsoft | x86/unicode_upper | |||
| NOD32 | ||||
| Norman | ||||
| nProtect | ||||
| Panda | ||||
| PCTools | ||||
| Prevx | ||||
| Rising | ||||
| Sophos | ||||
| SUPERAntiSpyware | ||||
| Symantec | ||||
| TheHacker | ||||
| TrendMicro | ||||
| TrendMicro-HouseCall | ||||
| VBA32 | ||||
| VIPRE | ||||
| ViRobot | ||||
| VirusBuster |
Commands
The following bash commands where used:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 | |
Results
Download: VirusTotal.com reports [PDF]
Download: Results [Output (PNG)] [Spreadsheet (xlsx)]
View: More Results (Old)
Below is only sample of the collect results. Sorry for the low resolution!
Table 1 - Results Summary

Table 2 - Anti-Virus Results
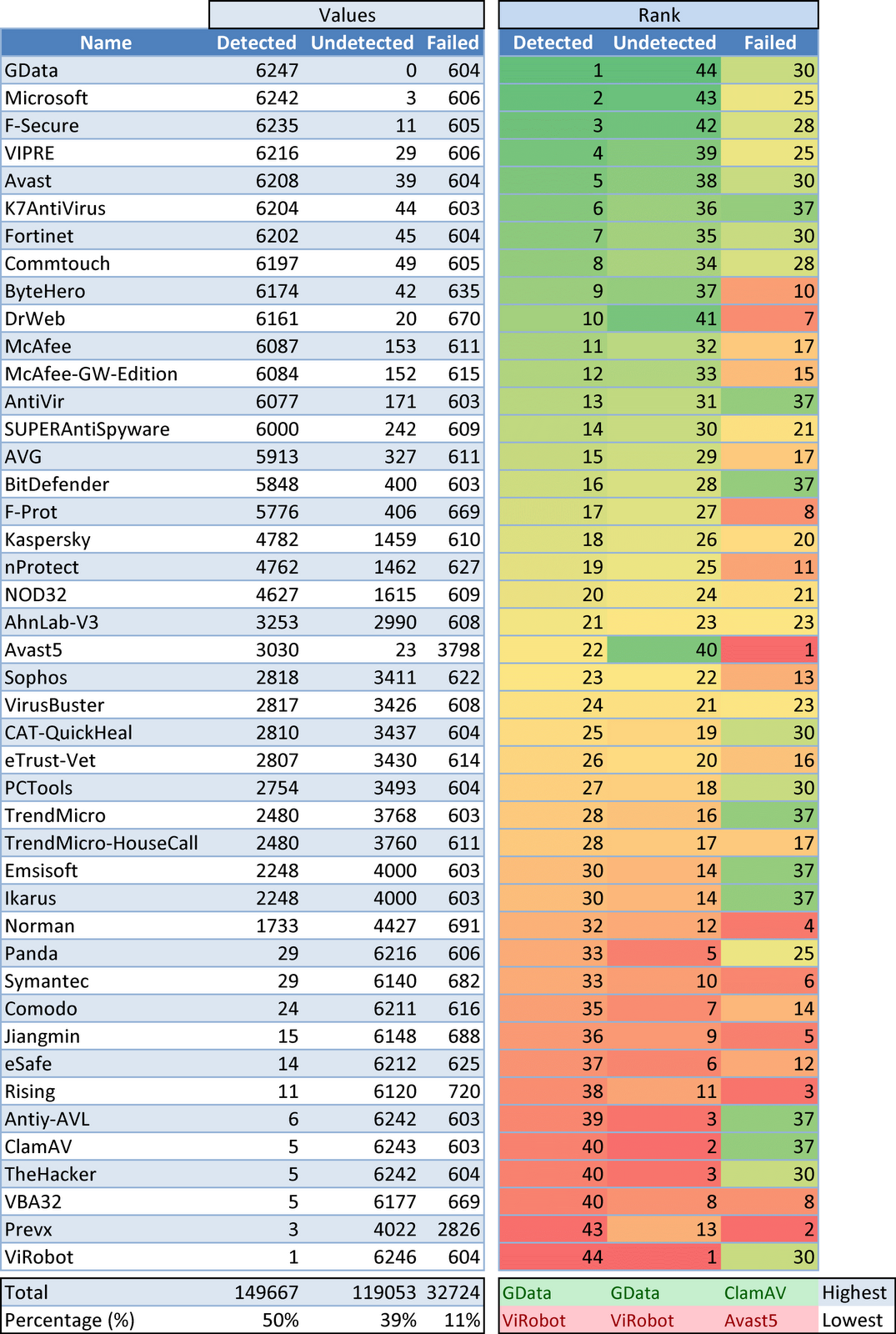
Graph 1 - Anti-Virus Performance
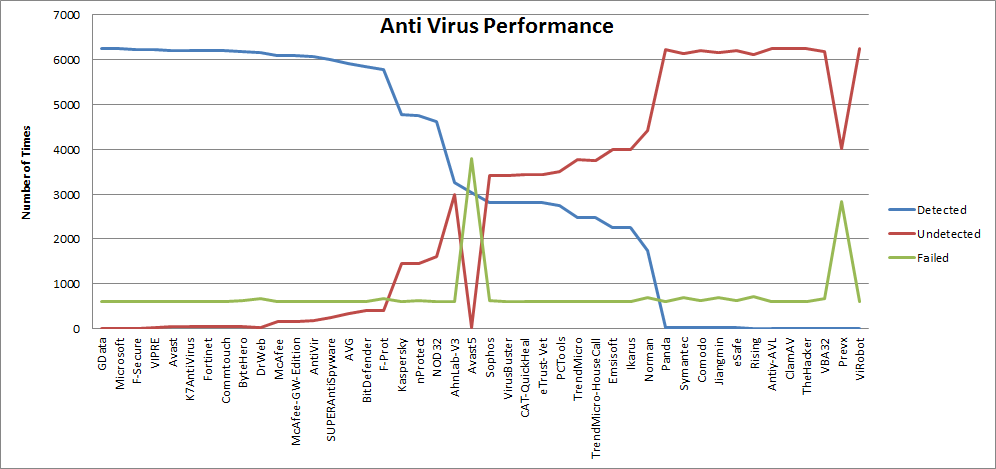
Graph 2 - Detection Rate for "generic/custom-calc.exe"
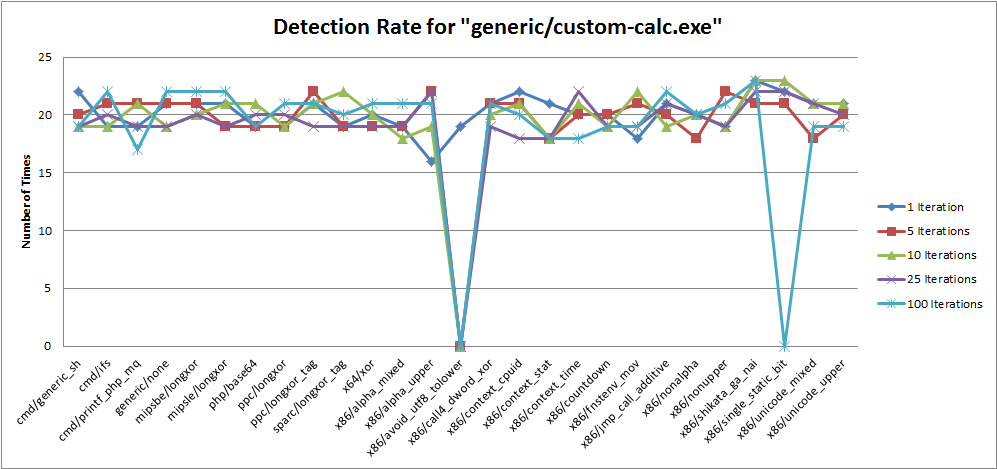
Graph 3 - Detection Rate for "OS Bind Shell"
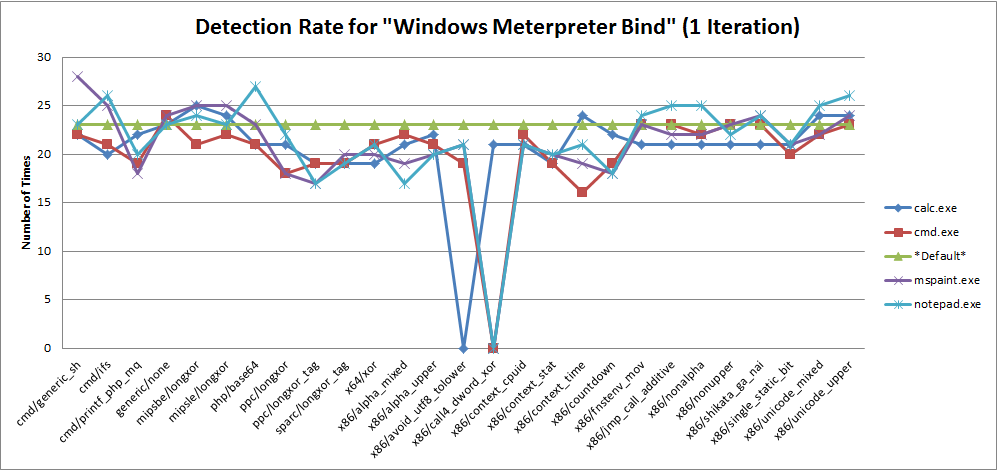
Graph 4 - Detection Rate for "Windows Meterpreter Bind (1 Iteration)"
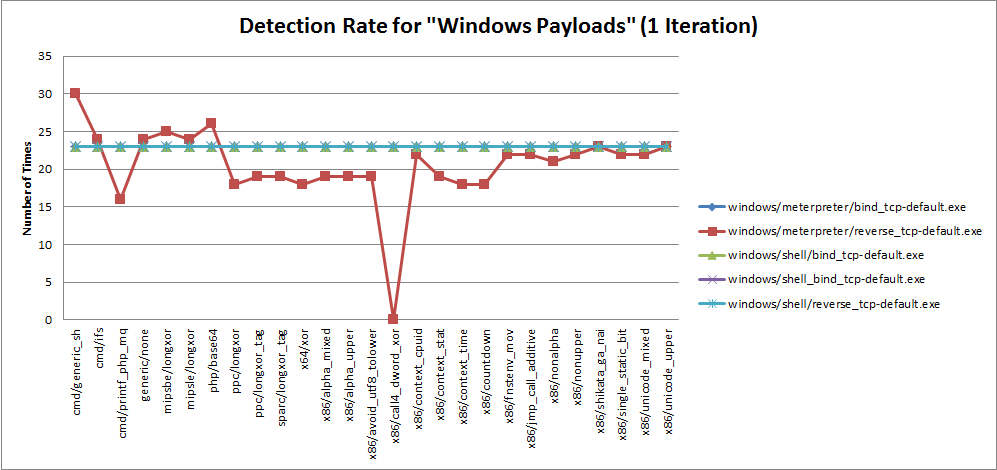
Graph 5 - Detection Rate for "Windows payloads (1 Iteration)"
Graph 6 - Iterations From 1 to 100
Graph 7 - Range of Encoders Efficiency
Graph 8 - Total Detects
Graph 9 - Total Rate Of Detection
Graph 10 - When Encoders Where Higher Than "generic/none"
Summary
- Wasn't able to use every template.
write.exe(wordpad) - failed to be encoded with every time.
- Wasn't able to use every encoder, every time.
- At 25 iterations -
x86/alpha_mixed&x86/alpha_uppertstop working. - At 100 iterations -
php/base64also stop working. x86/single_static_bitwas also unable to complete a couple of times.
- At 25 iterations -
- How do different encoders compare?
- Some are better than others; general use or for specific options.
- Is there a relationship with increasing the encoded amount of time, does it get detected less?
- No.
- By switching the payload, will this have an affect?
- Minor difference.
- If a different template was used, would it still detect the same amount of times?
- Minor difference.
- Does encoding make the file become detected more than if it wasn't encoded at all?
- Yes, it can do!
- Will the payload's operating system matter?
- Yes. Encoding didn't have a difference of Linux or OSX systems
- Which anti-virus product was able to detect the most (and the least) amount?
- GData &ViRobot respectively.
Conclusion
To take this further...
- What happens if the default values for the encoders were altered?
- What happens if multiple encoders were linked together to create a single output?